Cream of IT or the Cream of Chicken Soup?
Disclaimer: the following contents are from an email received by one of our readers who happens to be anonymous (aren’t they all?), apparently had a go at Focus Infocom. The email is presented in its entirety on this blog, and does not present any view, options or involvement by digitalsquid blog. The events presented in the following article may or may not be true and we cannot confirm it at the moment but it is interesting enough for us to present it in the blog for comments by our viewers and what they think. Further this mail has relevance to one of our articles in this blog titled "How Secure is ROL's high speed network? How Secure is your Data?" which is again one reason that the email is published. We stress that this email is published purely for discussion, and if actual , and if actually happened, maybe someone at focus infocom or anyone else might be able to shed light on the issue. Of coz we do not recommend that anyone tries this at home or elsewhere to see if it works. Comments are highly welcomed, but any comments that are directed personally and irrelevant to the topic will be removed.
--------------------------------------------------------
A previous article here has clearly hinted the real vulnerability in his article about the ROL's security issue. The dumb and the dumbers did not get an idea of what he has pointed out. Instead they pulled his tail taking some webserver issue and log2space issue which was not the real vulnerability or the security issue. After reading the article i thought i will give some try to see if it is true or close to true and to my amuzement, The ROL's network equipments can be managed by just anybody using SNMP.
Managing the Interfaces of the Routers! (Images are self explanatory in most cases)

A peak at the virtual pptp interfaces. The numbers beginning with ROL are ROL pptp usernames.
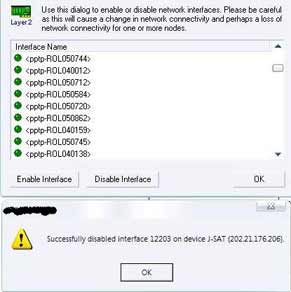
Tried to see if the interface can be disabled. Success!
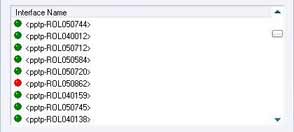
Disabled
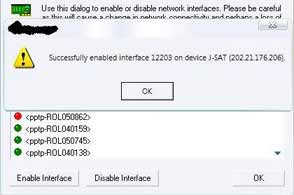
Re-enabling the interface.
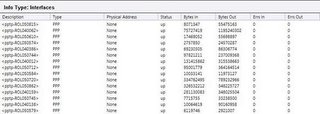
A glance at the traffic statistics of the pptp users.
A glance at the interfaces.
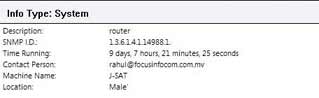
A glance at the system info.

Trying to disable Rahul’s pptp interface.
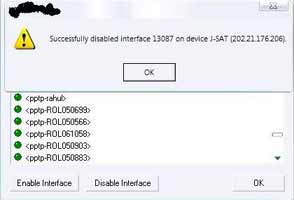
Succeed!!
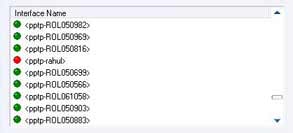
Disabled
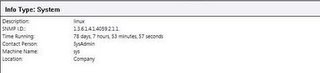
A glance at the system info of the linux machine.
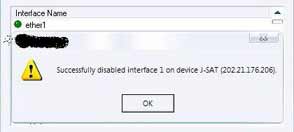
Disabling first Ethernet interface
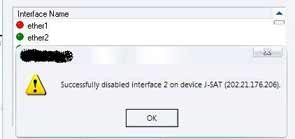
Disabling second Ethernet interface.A peak at the Cable Routers & their interfaces. The disabling of this interface led to lose the connectivity to JSAT side of the ROL’s network. At least it took them more than 4 hours to bring the network back to normal.

A glance at the interfaces.
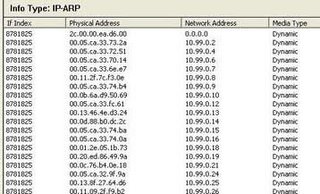
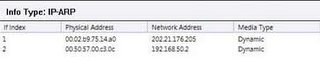
A glance at the ARP info.
Still more glances at the ARP.
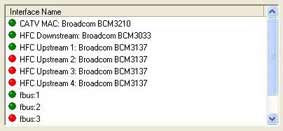
Disabling the upstream interfaces of the cable routers
 Disabling the internal interfaces (fbus1 and fbus2) and upstream interfaces and downstream interfaces.
Disabling the internal interfaces (fbus1 and fbus2) and upstream interfaces and downstream interfaces.
I hope ROL fixes this problem at the earliest
How Secure is ROL's high speed network? How Secure is your Data?
A boring week with nothing much to do or to celebrate, I connected a RF splitter to the J-SAT cable at our home to split the CATV cable and connected a cable modem. The cable did not lock as the power was way too low due to the splittings. We had another cable from MESCO which doesn’t have any splits. So I just split that into two and then connected the cable modem. Bingo, my modem signal is locked. Before I go any further let me try to give you all some info about the type of VPNs ROL uses now.
ROL is running on PPTP-VPNs now! What is a PPTP-VPN?
PPTP VPNs offer legacy authentication mechanisms such as PAP, CHAP, MS-CHAP, and MS-CHAPv2, with the strongest being MS-CHAPv2. MS-CHAPv2 is also used in Cisco’s LEAP and EAP-FAST phase-0. MS-CHAPv2 can be broken using the
ASLEAP cracking tool for Linux and Windows. A tutorial exploiting the weakness of PPTP-VPN with Asleap and Auditor can be found
herePPTP tunnels use an IP connection to form an encrypted tunnel for data transport. The tunnel has its own IP subnet (in the case of ROL, 202.21.*.*), and after the tunnel is formed between client and server, a static route is entered into both hosts so that all future data traffic is sent through the tunnel. However, the original IP subnet (in the case of ROL on jsat cable, 10.99.*.*) on the Hybrid Fibre Coax (HFC) network can still be used for data transfer, such as port scanners and other hacking tools. The high-speed connectivity over the HFC network not only makes it quicker, easier and cheaper for customers to get the service but also enables Whackers (black hat hackers) to enjoy a number of open ports and services that are in the pipeline. Without a personal firewall in place, the client and server devices are still open to IP attacks.
PPTP uses Microsoft Point-to-Point Encryption, which uses the RC4 stream cipher. While MPPE-128 is a reasonably strong encryption scheme, it’s the authentication mechanism (MS-CHAPv2) that makes PPTP weak.
Connecting to ROL HFC Network:Then I connected an Ethernet cable between my laptop and the modem and got an IP from the 10.99. range (original IP subnet). Fired up Nmap to see if there are any open ports and found some machines with port 80 open, ran Firefox and connected to one of those machines. Firefox brought me to a web page of some sort of web server called
WAMPP with access to a MySQL database. I was even able to create my own databases without any authentications. Could this be a machine of an individual user? Could this be a machine of ROL? I leave it for the readers to do their own research and find out for themselves. (Hint: There are other interesting ports too!)
Before turning my mind to other interesting ports. I got stumbled into ROL’s Subscriber Management Software which runs on IP 202.21.176.234 externally and IP 192.168.50.1 internally. They run really interesting software called
Log2Space from Spacecom Technologies Limited, India. Those of you who are interested in learning how this software works could see a demo of it on the Spacecom website. Click
here for a demo.
Did some further scanning and ran a couple of tools by pressing keys and buttons here and there and I couldn’t even believe my eyes on where I end up. Where was I walking into wearing the dark black court? In fact I was in a position to map the whole network with more than 20 different segments and was also in a position to throw off individual users or a whole bunch of users from the network by pressing a couple of buttons. For those of you who are interested in the logical design of the ROL network may
download this Visio network map of ROL.
For a second I thought, is this the security we talk about? Is this the industry standards and practices that ROL follows as required of an ISP (Internet Service Provider)?
A word to the tech team at ROL: Don’t mislead your Managing Director in to thinking that you have the best security that is up to the industry standards. Humans do make mistakes. Humans learn by their mistakes. So admit your mistakes to your boss, get the issues resolved internally or externally and then learn from that experience rather than trying to hide the facts and mislead your own boss. If you mislead him, he will unknowingly mislead the general public.
Some of us might think that we need a rocket scientist who has a law degree to perform such a task but in reality somebody who has a little bit of networking knowledge with a few network tools could perform such a task in a few minutes.
Dhiraagu Mail Server Issues/ Focus VPN...
Just an update.. dhiraagu is appreantly having some major issues with their mailservers.... focus is implementing VPN for all its customers.. no more free internet...more on these issues sooon...
ta for now

















 Disabling the internal interfaces (fbus1 and fbus2) and upstream interfaces and downstream interfaces.
Disabling the internal interfaces (fbus1 and fbus2) and upstream interfaces and downstream interfaces. 



